Plaintext HELLO Autokey N Ciphertext ULPWZ Example-2. AES is the successor to 3DES and DES and is the best choice for a symmetric encryption algorithm.
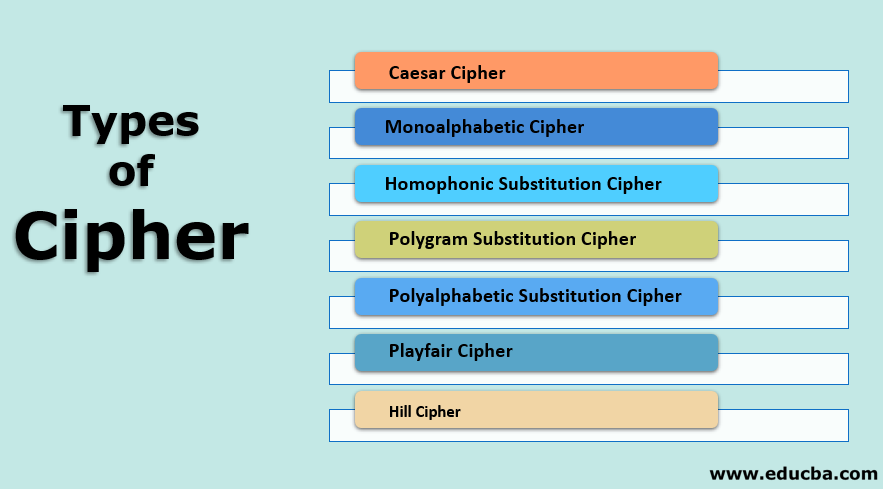
Types Of Cipher Learn Top 7 Various Types Of Cipher In Depth
Asymmetric ciphers are often used to encrypt emails.

. When a block cipher is used for encryption and decryption purposes the message is divided into blocks of bits. Good stream ciphers offer the following. Symmetric Ciphers Questions and Answers Substitution and Transposition.
On multiplying this matrix with the mix columns matrix we get the identity matrix this proves that it is an. Integrated Encryption Schemes Integrated encryption schemes IESare modern public key encryption schemes which combine symmetric ciphers asymmetric ciphers and key-derivation algorithms to provide secure public-key based encryptionPKE. 7 The Feistel Cipher The modern block cipher was invented by Horst Feistel around 1973.
Part of this shuffling process involves a function called f f which is used to combine half of the text being enciphered with a key from the key schedule. Triple DES is a later version of DES that performs three rounds of encryption. Kevin is configuring a web server to use digital certificates.
RSA is a secure algorithm but it is asymmetric rather than symmetric. When we moved from the WEP encryption to WPA2 on our wireless networks AES was a big part of that encryption standard. The two types of traditional symmetric ciphers are Substitution Cipher and Transposition Cipher.
The goal of this type of algorithm is to achieve confusion and diffusion in the encrypted text. Symmetric Cryptography By Rafael. A 3DES takes longer due to the higher processing power required.
These blocks are then put through mathematical functions one block at a time. 7 is a symmetric stream cipher A DES B AES C RC4 D twofish Ans C Section 1541 Course Hero 7 is a symmetric stream cipher a des b aes c rc4 d School Arizona State University Course Title CSE 430 Type Test Prep Uploaded By RyanD392 Pages 7 Ratings 100 17 This preview shows page 2 - 6 out of 7 pages. Ciphers or algorithms can be either symmetric or asymmetric.
Symmetric ciphers are just as secure as asymmetric ciphers but with smaller keys. Good for databases and small bits of data. Describe Electronic Code Book ECB related to symmetric block ciphers.
RSA is based on factoring composite numbers into their primes and ElGamal is based on discrete logarithms. Repeat the process for all alphabet in plain text. A symmetric key cipher also called a secret-key cipher or a one-key cipher or a private-key cipher or a shared-key cipher Shared_secretis one that uses the same necessarily secret key to encrypt messages as it does to decrypt messages.
Symmetric key ciphers where a block of data is encrypted. Both methods provide roughly the same strength per bit and are far weaker per bit than ECC. Unpredictable statistical results long periods.
For any block of plaintext the cipher is always the same eg. It was invented by Blaise de Vigenère in 1586. Which of the following is not true regarding symmetric or asymmetric ciphers.
The following flowchart categories the traditional ciphers. Based on the concept of a product cipher which uses two or more basic ciphers in sequence in such a way that the combined result is cryptographically stronger than any of the component ciphers. ECB uses padding for leftover space in the 64-bit blocks.
Is the following matrix the inverse matrix of the matrix used in the mix columns step. Symmetric ciphers questions and answers 1. These algorithms also called ciphers are efficient to encrypt high volumes of data.
In general more secure than the Vigenere cipher. Triple DES or 3DES is symmetric algorithm which means they key used to encrypt is identical to the key used to decrypt. Start your trial now.
Symmetric ciphers are generally faster than. Substitution Ciphers are further divided into Mono-alphabetic Cipher and Poly-alphabetic Cipher. First week only 499.
Abc will always equal fct. Asymmetric ciphers are almost always used to encrypt hard drives or files. Symmetric cryptography is about algorithms that use the same keyword to encrypt and decrypt information.
In monoalphabetic each alphabet in plain text can be replaced by any other alphabet except the original alphabet. It is closely related to the Vigenere cipher but uses a different method of generating the key. X3 1 x x x3 1 a Yes b No c Cant say d Insufficient Information Answer.
View full document Document preview. WRONG B is incorrect because AES is a symmetric block cipher. As Caesar cipher and a modified version of Caesar cipher is easy to break monoalphabetic cipher comes into the picture.
Symmetric ones use the same key called a secret key or private key for transforming the original message called plaintext into ciphertext and vice versa. ECC EI Gamai 3DES RSA Explanation. Youll see this used in WPA2.
714 Feistel Cipher A Feistel cipher is a cipher that enciphers the plaintext in rounds by splitting the information up like a deck of cards and shuffling it around. View Symmetric Ciphers Questions and Answersdocx from CSE 418 at International Institute of Information Technology. At the time he was working for IBM.
Examples of such asymmetric encryption schemes are. Autokey Cipher is a polyalphabetic substitution cipher. Choose from among the following cipher systems from best to the worst with respect to ease of decryption using frequency analysis.
Solution for Symmetric key ciphers - Include the notes needed to encrypt or decrypt each of the following ciphers. For symmetric key ciphers K aK b - Only Alice and Bob knows K a or K b - Eve has access to E D and the Communication Channel but does not know the key K a or K b E K a D K b Communication Message Channel Message Eve Alice Bob Types of symmetric key ciphers Block Ciphers. First lets study about mono-alphabetic cipher.
Symmetric ciphers are faster than asymmetric ciphers. Works with a block of data at a time. Which algorithm is a symmetric cipher.
AES is a symmetric cipher and symmetric ciphers are not used in digital signatures. Weve got the study and writing resources you need for your assignments. Symmetric ciphers are ciphers that use the same key to encrypt and decrypt ie for both the encryption and decryption algorithms.
A symmetric cipher is one that uses the same key for encryption and decryption. This is a 128-bit block symmetric cipher and they have different key sizes that you can use anywhere from a 128-bit up to a 256-bit key size on both sides of this symmetric cipher.
Cipher Definition Types Facts Britannica

Pin By Danielamalagyiova Alexander Ma On Vytlacit Morse Code Words Magic Squares Math Magic Squares

Encryption Via A One Time Pad One Time Pad Cryptography Coding

0 Comments